Microcorruption
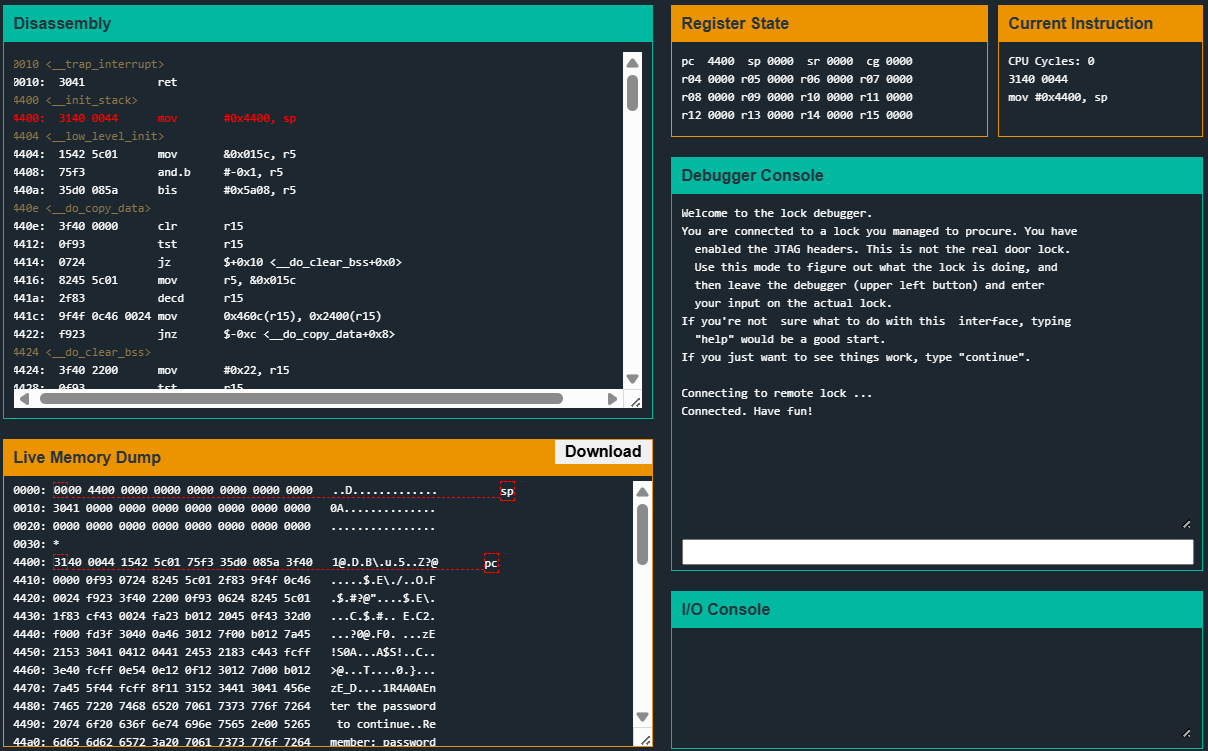
A year or so ago I came across Microcorruption, a website hosting a set of exercises/challenges where you are supposed to reverse-engineer an MSP430-based embedded device (a lock which they call the “LockIT Pro”) using a debugger, and bookmarked it with all the best intentions to play around with the exercises… I then proceeded to completely forget about it until recently when I was cleaning up my bookmarks.
Now I want to devote some time to play around with the CTF exercises and see how far I get.
The website gives you everything you need - an emulated environment, access to a rudimentary debugger, the assembly code, a memory viewer, console output, and the registers. They also provide links to the MSP430 ABI and User Guide (useful to figure out register map of the device, instruction set, interrupt vector, etc.), as well as LockIT Pro’s manual/user guide which describes the platform that you’re working with.
As I work through the different exercises, I will be posting writeups and solutions in the following GitHub Repository .